Leave us your email address and be the first to receive a notification when Robin posts a new blog.
As the title already suggest, in this blog we want to forward events for NSX IDS/IPS. If you have missed one of the previous steps of NSX-T IDS/IP, you can check them here:
- NSX-T IDS/IPS overview
- NSX-T IDS/IPS installation
- NSX-T IDS/IPS creating rules
- NSX-T IDS/IPS testing
- NSX-T IDS/IPS event forwarding (this blog)
NSX-T IDS/IPS forwarding events
To be able to respond to the events you may need to forward the events from NSX to a central SIEM or syslog target. As said, we don’t want to stare at the NSX-T GUI all day.
The NSX documentation gives you a hint on how to forward the events.
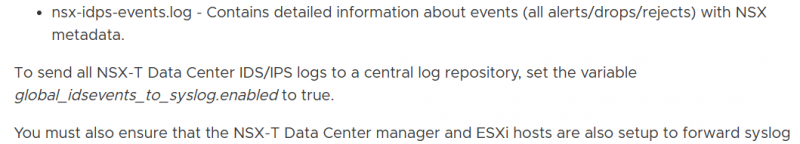
Unfortunately, the documentation doesn’t tell you where to set this global_idsevents_to_syslog.enabled setting.
It looks like a setting that needs to be set in a config file or probably thru an API. But the API guide or a quick Google did not reveal the answer quickly. Even if you know the answer there aren’t many references to the setting. So, hopefully this blog will help in finding this setting.
Eventually I found my answer in the documentation for the IDS/IPS Proof of value, I mentioned in earlier blogs. The setting needs to be adjusted with an API call to /api/v1/global-configs/IdsGlobalConfig
But let’s start with some basics. As with the Distributed Firewall the IDS/IPS log and events are generated on the ESXi hosts and can be forwarded from there. For the Distributed Firewall the log file is /var/log/dfwpktlogs.log.
Forwarding of the logging on the ESXi hosts can be done thru the advanced settings.
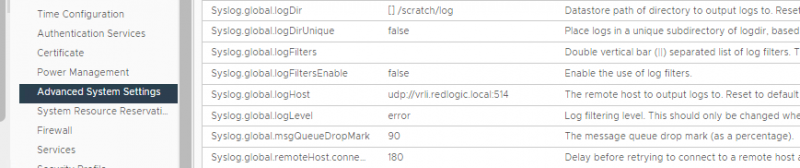
The log files for IDS/IPS are stored in a separate directory /var/log/nsx-idps. But since there isn’t much information in the files on the ESXi hosts, there also isn’t much information forwarded to the syslog server. Time to adjust the global_idsevents_to_syslog.enabled setting.
The first step is to perform a GET request against the NSX manager for the API call /api/v1/global-configs/IdsGlobalConfig. I prefer to use Postman for this.
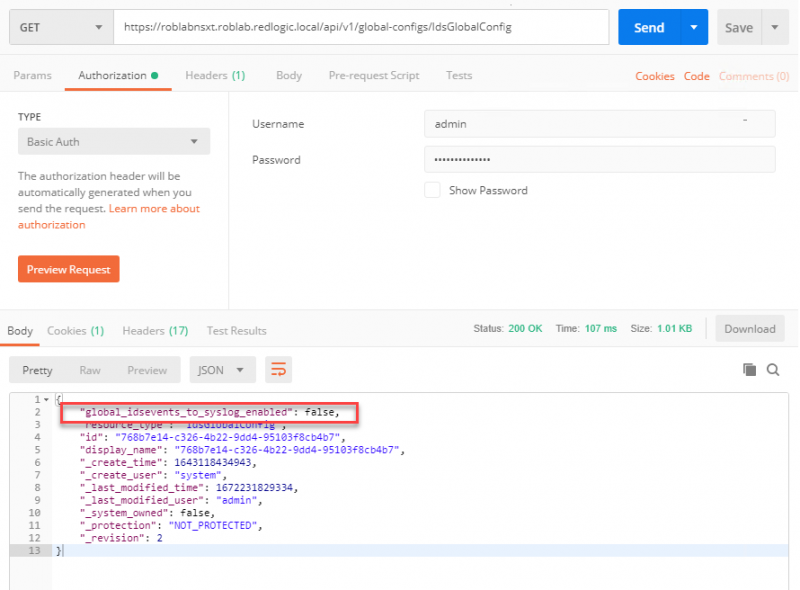
As you can see the setting for forwarding the idsevents is set to false. Copy the top 2 line and the _revision line into a new JSON file and set the idsevents setting to true.
{
"global_idsevents_to_syslog_enabled": true,
"resource_type": "IdsGlobalConfig",
"_revision": 2
}
With this JSON call add the same API call but with a PUT action, this will update the idsevents setting.
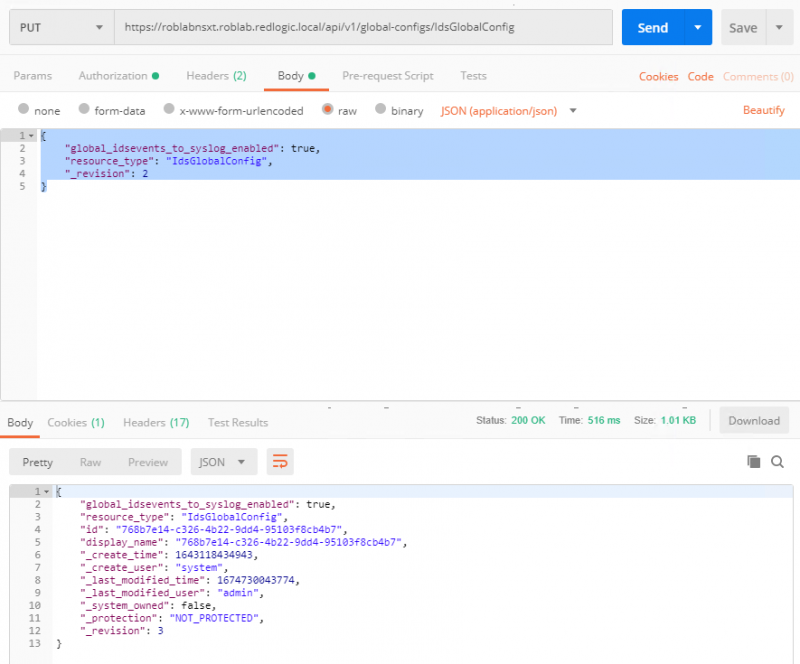
If we now trigger the same druppal attack as we have done in the previous blog. We can see the events appearing in the /var/log/nsx-idps/nsx-idps-events.log file on the ESXi host. Since we have log forwarding configured on the ESXi host we can also see the events in log insight or a SIEM system.
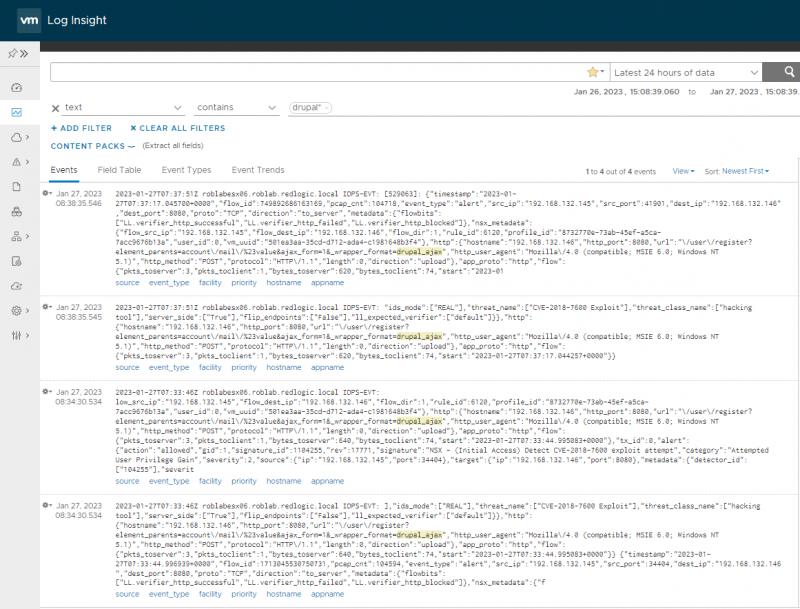
As said, hopefully this blog will help in finding the setting to forward IDS/IPS events from NSX to a syslog target. This is it for now in this blog series, I’m experimenting with other IDS/IPS testing tools, so maybe there will be some future follow-ups.
Hopefully, you have enjoyed reading this blog. If you have any questions or would like to see some more, please leave them at the bottom.
Questions, Remarks & Comments
If you have any questions and need more clarification, we are more than happy to dig deeper. Any comments are also appreciated. You can either post it online or send it directly to the author, it’s your choice.





 LinkedIn
LinkedIn
 Twitter
Twitter