Leave us your email address and be the first to receive a notification when Robin posts a new blog.
One of the most important best practices, for the NSX Distributed Firewall, must be: the Applied To. I explain in this blog why the “Applied To” is so important for the inner working process and performance of the NSX Distributed Firewall.
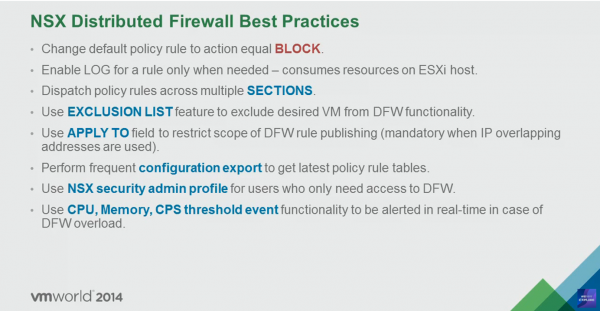
Applied To has been around since the early days of NSX micro-segmentation. At least, I found this image that dates from VMworld 2014.
In this first part of the blog I explain the basics. Are you already familiar with this? The second part of this blog will appear next week, in which I will tell you all about the technical details behind the Applied To setting in the NSX Distributed Firewall.
Follow me (at top of this page) to be notified first.
Too technical? Let's start with the basics.
The basics behind Applied To
Applied To is used to limit the scope of published firewall rules. What does that mean? Perhaps this can best be explained with an example. In the situation below we have several countries. And each country has its own physical firewall.
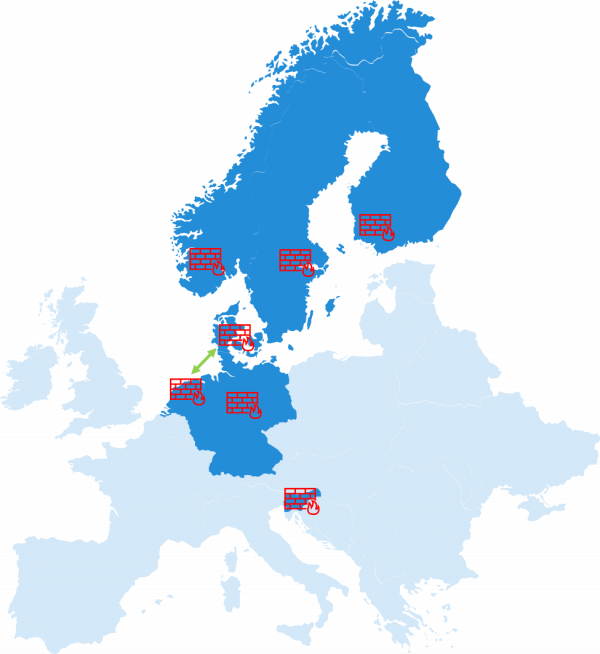
When we want to allow a connection from the Netherlands to Denmark or vice versa. We only need to create a firewall rule on both of these firewalls. The firewalls in the other countries can skip this rule, because the traffic never gets through them. Programming the firewall rule in the other countries would just require unnecessary processing power, because it needs to be checked.
The NSX Distributed Firewall has a management plane, that is used to program the firewall rules in the data plane. The management plane for the distributed firewall is on the NSX managers. For the data plane it is on the vSphere ESXi hosts. Where each vNic of the virtual machines has its own firewall rule set. This firewall rule set on the vNic can be compared to the firewalls for each country in the example.
Applied To Example
The result of programming the firewall rules in NSX is best shown with an example. The following rule is present in the NSX management plane and the Security Group membership of the VMs is as follows:
- Three rules have been applied to the entire Distributed Firewall rule base.
- And two rules applied to a specific application.
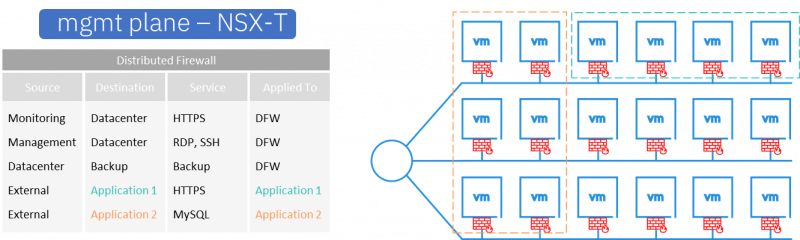
This would produce the following result for the VMs in the specified Security Groups in the data plane on the ESXi hosts.
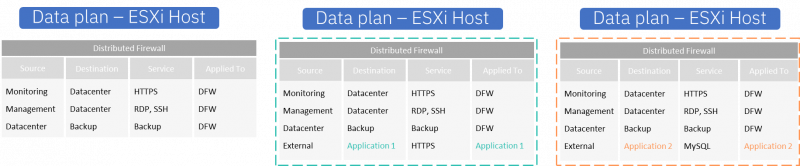
The VM that is not part of a Security Group receives only 3 firewall rules. While the VMs that are part of one of the application Security Groups receive an additional rule. But only the rule applied to the specific application Security Group of which the VM is a member.
In this example, the difference between the management and data plane is not that big. But imagine you have a live environment with 300 applications, each with at least 10 firewall rules. If these rules were applied to the entire DFW, each VMs would receive more than 3000 rules on their vNIC. Whereas if the applied is set to each application, the VMs would only receive 10 rules and that makes a big difference in the processing. Especially if you work with latency-sensitive applications.
Take away
As you can see, the Applied To helps significantly reduce the number of firewall rules in the data plane. Most rules are used against Applications or Environments and therefore should only be applied to those Security Groups. For shared services such as monitoring tools or a remote access tool, that needs access to all VMs within NSX, the Applied To can be set to the entire DFW.
So, remember to scope the firewall rules in the Distributed Firewall as much as possible. There is nothing wrong with applying a firewall rule to the entire DFW, but use it with care and plan your firewall rules accordingly.
Hopefully you enjoyed reading this blog. Next week I will tell you all about the technical details behind the Applied To setting in the NSX Distributed Firewall, in part 2.
If you have any questions or would like to see more? Just leave a comment below.
Questions, Remarks & Comments
If you have any questions and need more clarification, we are more than happy to dig deeper. Any comments are also appreciated. You can either post it online or send it directly to the author, it’s your choice.





 LinkedIn
LinkedIn
 Twitter
Twitter