Leave us your email address and be the first to receive a notification when Robin posts a new blog.
As the title of this blog already suggest this blog will show the steps to create rules in NSX-T to enable IDS or IDS/IPS on specific VM's. If you have missed one of the previous steps of NSX-T IDS/IPS or wish to jump directly to another part, you can do it here:
- NSX-T IDS/IPS overview
- NSX-T IDS/IPS installation
- NSX-T IDS/IPS creating rules (this blog)
- NSX-T IDS/IPS testing
- NSX-T Event forwarding
NSX-T IDS/IPS creating rules
Now that the hosts are enabled for the use of IDS/IPS we can start creating rules. If you are only using the IDS/IPS functionality, as I’m doing for this blog, you can ignore the yellow banner about malware prevention at the top of the page. Hopefully VMware will create a ‘do not show again’ button like they did for the Identity based firewall settings in NSX-T 4.0.
Before creating IDS/IPS rules it is best to have a look at the profiles for IDS/IPS under Security > Policy Management > IDS/IPS & Malware Prevention > Profiles. The IDS/IPS profile allows you to specify for which type of attack or which severity you want to monitor and prevent. For example, you can monitor only for Critical severities like in the default IDS profile. But you can also filter on attack types, targets or a CVSS score.
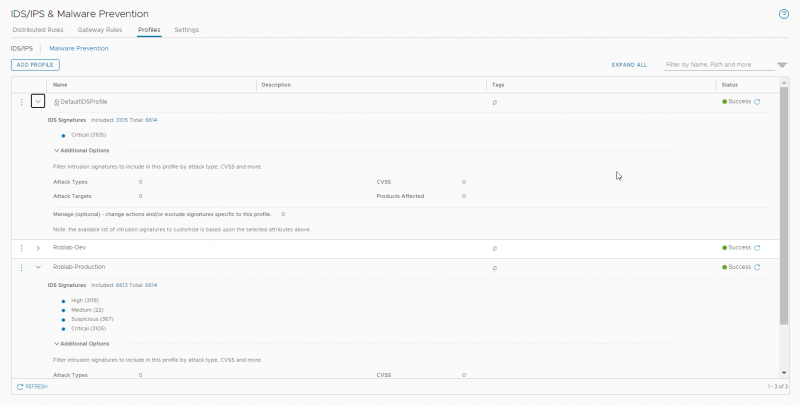
For this lab I created an additional profile that monitors for all intrusion severities except the low ones. With this profile we will be making the IDS/IPS rules under Security > Policy Management > IDS/IPS & Malware Prevention > Distributed rules.
The creating of IDS/IPS rules works like the creation of distributed firewall rules. First you create a Policy and give it a name. The Policy can then have one or multiple rules.
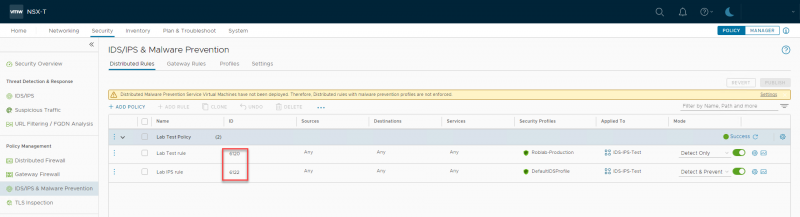
In this example I have created a policy with two rules. The first rule is an IDS rule with mode ‘Detect Only’ that uses the custom created profile. So, it should alert on any severity it detects except for the low ones.
The second rule is an IDS/IPS rule with mode ‘Detect & Prevent’ that uses the default IDS profile. So, it should alert and block all critical severities.
Both rules have been applied to a group I created which has two member VM's.
Verifying the configuration
We can now check the status of the IDS again from the NSX command line using get ids … commands. These commands should be run on the ESXi host that has the VM's running where the IDS/IPS rules are applied to. For the lab setup I created a DRS rule to pin the two VM's to a specific ESXi host.
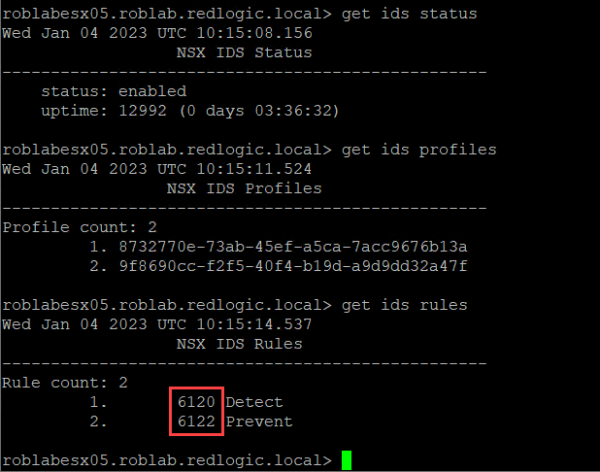
As you can see the status is now enabled and the profiles and rules can be seen. The IDS rule numbers (6120 & 6122) correspond with the rules in the NSX GUI in the same manner the Distributed firewall rules can be matched.
Now that we have created the rules we can sit back and wait for an attack or vulnerability to be found. But since this lab doesn’t contain any VM's directly connected to the internet, we might be waiting for a long time.
Although the wish is not to see any attacks or vulnerabilities in a production environment. We do want to know if the solution is working. For now, all we can see under Security > Threat Detection & Response > IDS/IPS is ‘No Intrusions Detected’
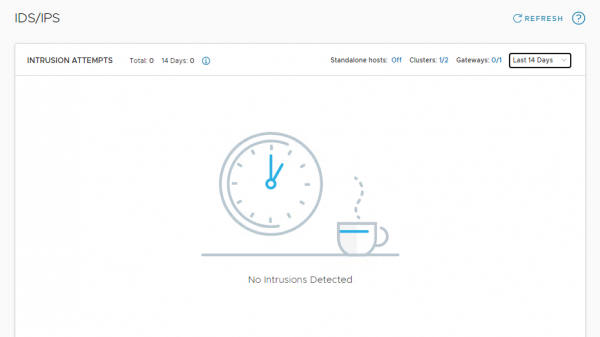
Fortunately, there are some test VM's available, and the VMware NSBU also created some test scenarios and a Proof of Value on github. I’m not sure if you can still sign up for the proof of value but at least I thought it was a good idea to use the tests to show the setup is working.
But that is fuel for the next episode NSX-T IDS/IPS testing
Hopefully, you have enjoyed reading this blog. If you have any questions or would like to see some more, please leave them at the bottom.
Questions, Remarks & Comments
If you have any questions and need more clarification, we are more than happy to dig deeper. Any comments are also appreciated. You can either post it online or send it directly to the author, it’s your choice.





 LinkedIn
LinkedIn
 Twitter
Twitter