Leave us your email address and be the first to receive a notification when Robin posts a new blog.
As the title of this blog already suggests this is an overview of NSX-T IDS/IPS. In the next couple of blogs, I will be installing and trying to test the solution in our lab environment.
Before diving into the technology, or the way VMware has implemented IDS/IPS in NXS-T, I wanted to provide a small overview of what IDS/IPS is. Most of it can also be found on the internet. So, if you are already familiar with IDS/IPS you can scroll to the requirements below or jump straight to one of the following topics:
- NSX-T IDS/IPS overview (this blog)
- NSX-T IDS/IPS installation
- NSX-T IDS/IPS creating rules
- NSX-T IDS/IPS testing
- NSX-T Event forwarding
NSX-T IDS/IPS overview
IDS/IPS stands for intrusion detection system (IDS) and intrusion prevention system (IPS). Where IDS can detect and alert on a threat or malicious activity in the network traffic, IPS also has the possibility to prevent or block the network traffic based on the findings of IDS. An IDS/IPS solution sort of continues where the classic firewall stops. A classic firewall allows traffic based on the port number and sometimes on the protocol (Layer-7 or firewall). But a classic firewall doesn’t continuously look at the network traffic. For example, once it has determined the port number is 443 TCP or the protocol is HTTPs, based on the first x number of packets, it allows the traffic and doesn’t look at it again until a new session is established.
An IDS continuously looks at the network traffic to see if there is a threat or malicious activity. Based on knowledge it has on the network traffic, it can alert on threats or malicious activity to an IPS or a Security Information and Event Management (SIEM) system. In the case of a SIEM the Security Operations Center (SOC) can take actions to investigate the alert. If an IPS is also in place it can take the action to block the traffic instantly. Therefore, an IPS always needs to be placed in-line with the network flow to be able to block it.
IDS works by looking for specific patterns in the network traffic based on signatures or by looking at anomalies. Signature based inspection is to detect known threats and anomaly-based inspection is to detect unknown treats.
In contrast to the classic firewalls IDS/IPS can also be available in next-generation firewalls, at least in some form. And in most datacenters the classic firewall has been replaced by a next-generation firewall. So why does VMware build the IDS/IPS functionality into NSX-T?
IDS/IPS functionality in NSX-T
For the same or similar reasons, the Distributed Firewall (DFW) was introduced, VMware has also developed the Distributed IDS/IPS functionality. As said in the overview, for the IPS to work, the traffic needs to flow thru it. Thus, it works perfectly for traffic flowing in and out of a cloud or datacenter, but a normal IPS or next-generation firewall can’t protect the traffic within the cloud or datacenter. At least not without difficult network topologies. Especially if you are using modern micro services applications. The power of IDS/IPS in NSX-T is that it is distributed.
The distributed IDS/IPS functionality in NSX-T works on the same place in the vSphere environment as the distributed firewall, on the virtual Nic of the virtual machine.
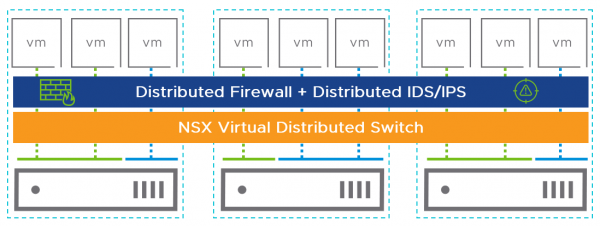
This architecture makes it easier to implement, since no network changes are required to route the traffic thru an appliance (Physical IDS/IPS or NGFW) avoiding hair-pinning of traffic.
From NSX-T 3.2 VMware uses multiple sources to update the signatures used in their solution. Signatures from Trustwave Spiderlab and Emerging Treat are combined and tested by VMware. The signatures are updated daily to detect all known threats. Before NSX-T 3.2 VMware only used signature-based detection and therefore could only detect known threats.
To detect unknown threats, starting from NSX-T 3.2, VMware has introduced what they call Behavioral IDS/IPS. Based on LUA (cross platform programming language) scripts NSX-T IDS/IPS detects unusual behavior and possible zero-day attacks.
NSX-T IDS/IPS requirements
Let’s have a look at what we need to use IDS/IPS within NSX-T. To be able to install or enable IDS/IPS in NSX-T, you need to have NSX-T up and running and the correct license (of course). And there it gets a little complicated. But before we talk about the license, something important is, that you do not need to have NSX Application Platform (NAPP) or the NSX Intelligence to use IDS/IPS. Somehow a lot of people don’t want to use IDS/IPS because of the additional NAPP that needs to be installed and maintained. Now for the license:
IDS-IPS is part of the NSX xxxx Firewall with Threat Prevention, where the xxxx can stand for Distributed or Gateway or it can be purchased as an add-on NSX Threat Prevention Add-On for NSX Distributed Firewall.
There is also and Advanced Threat Prevention license for malware prevention and Network Traffic Analysis (NTA). For these functions you do need to use NAPP.
Both IDS/IPS and malware prevention can be combined to be used in the Network Detection and Response (NDR) cloud solution VMware offers, but that’s a little out of scope for this blog series.
Back to the NSX-T license for IDS/IPS. As shown on the page NSX-T Knowledge base article 86095
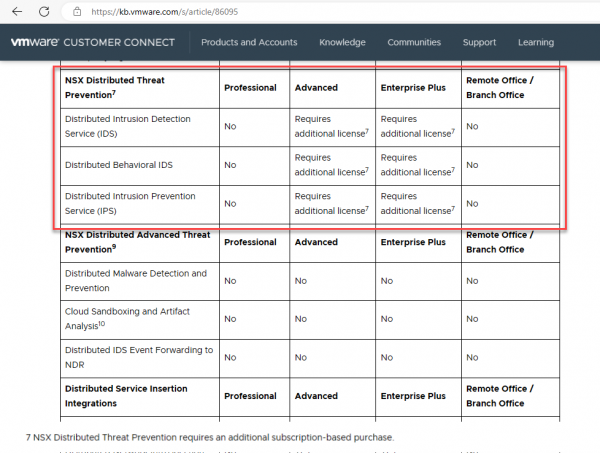
IDS/IPS is part of NSX distributed threats prevention and requires either a subscription on top of the perpetual NSX-T Advanced or Enterprise plus license or a Security License that is subscription based.
But please, double check this information with your VMware reseller as there are many changes in licensing modes lately and I’m not a license specialist.
For my lab I’m using a NSX-T Evaluation license as found in the VMUG advantage subscription or the vExperts program.
Now that we know a little about IDS/IPS and the requirements, it's time to start deploying IDS/IPS into our lab environment.
Next step is the NSX-T IDS/IPS installation
Hopefully, you have enjoyed reading this blog. If you have any questions or would like to see some more, please leave them at the bottom.
Questions, Remarks & Comments
If you have any questions and need more clarification, we are more than happy to dig deeper. Any comments are also appreciated. You can either post it online or send it directly to the author, it’s your choice.





 LinkedIn
LinkedIn
 Twitter
Twitter