Leave us your email address and be the first to receive a notification when Robin posts a new blog.
Since I put a lot of information into my session, I decided to split the information into 3 smaller blog posts. When the recorded session becomes available, I will update this blog with a direct link.
Updated March 2022 : The VMUG NL session can be viewed here and this is the direct link to my session.
Information on Host Migration, as discussed in my VMUG session, can be found in these previous NSX V2T migration blog posts:
Okay, so much for the introduction. Let’s get started.
In the previous blog post I stopped at the point where the configuration was migrated into NSX-T. Although migrating the configuration into NSX-T is a non-disruptive action, it is not completely without risk. Because the Tier-0 gateways are also created in the NSX-T edge nodes, some additional attention should be given. To make sure the connection towards the Tier-0 gateway doesn’t become active the uplinks on the NSX-T Edge nodes are down. So, take special care not to accidentally reboot these NSX-T edge nodes, because then the Tier-0 gateway will become active with duplicate IP-addresses. As they have the same configuration as the NSX-V ESGs.
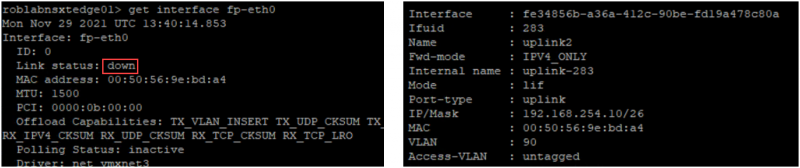
As shown in the screenshots the fast-past interfaces on the NSX-T edge node have been set down. The uplink for the Tier-0 gateway is already configured but isn’t reachable because the interfaces on the NSX-T edge nodes are down.
NSX V2T Edge Migration
After the NSX-V has been imported, analysed and created in the NSX-T manager. The next step is to migrate the North/South traffic from NSX-V to NSX-T.
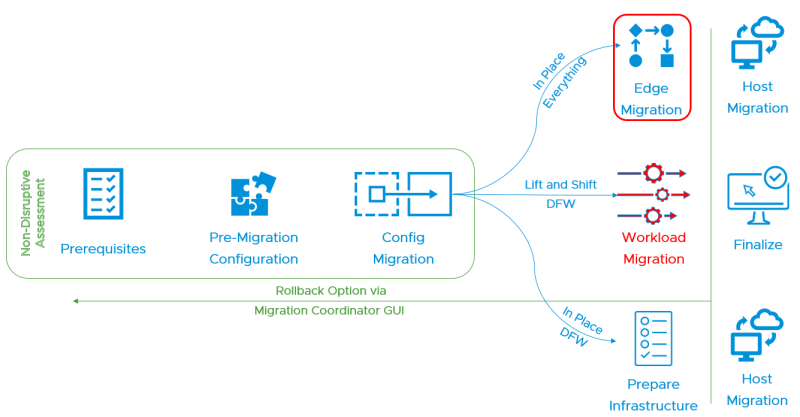
To make this step a little more visible I used the following drawing in my presentation:
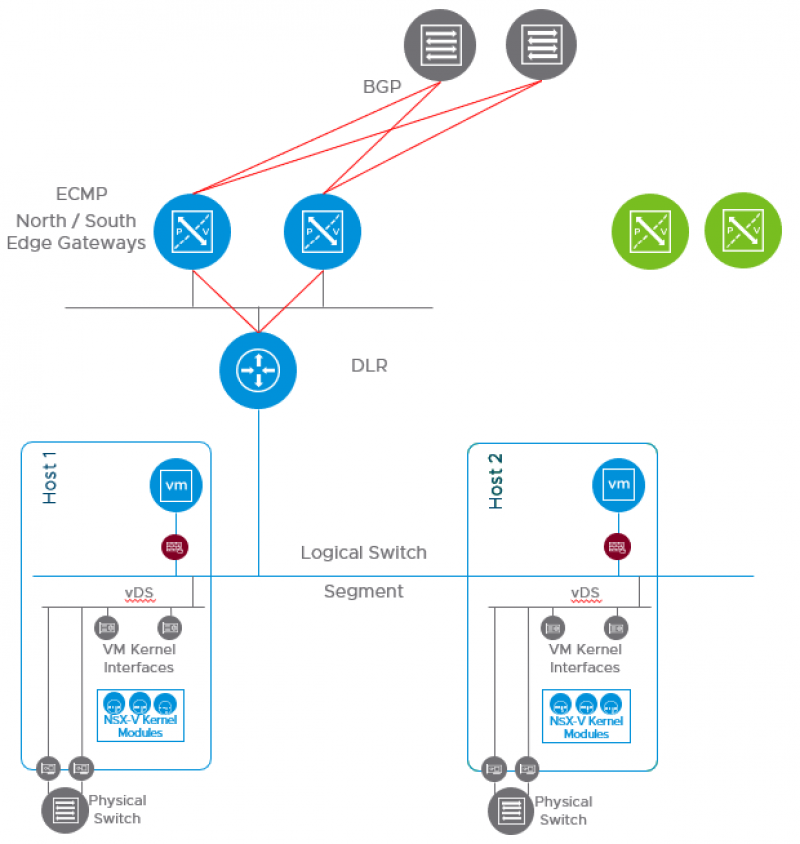
On the left you can see the NSX-V DLR in blue and the NSX-V ECMP ESGs above it. The ESGs have a BGP peering with the physical upstream routers to the North and with the DLR to the South. Both hosts are still prepared with NSX-V.
When the Edge migration is started, the following actions are taken by the migration coordinator:
- Controller Disconnected Operation (CDO) is enabled.
If it wasn’t already. - The DLR receives a static route to the NSX-T Tier-0 gateway
- The NSX-V Controllers are shut down
- All NSX-V ESG edge receive a block all traffic rule
- The NSX-T Edge interfaces are brought up
- The BGP peering become Established between the Tier-0 gateways
After this step has been completed the lab environment looks like this:
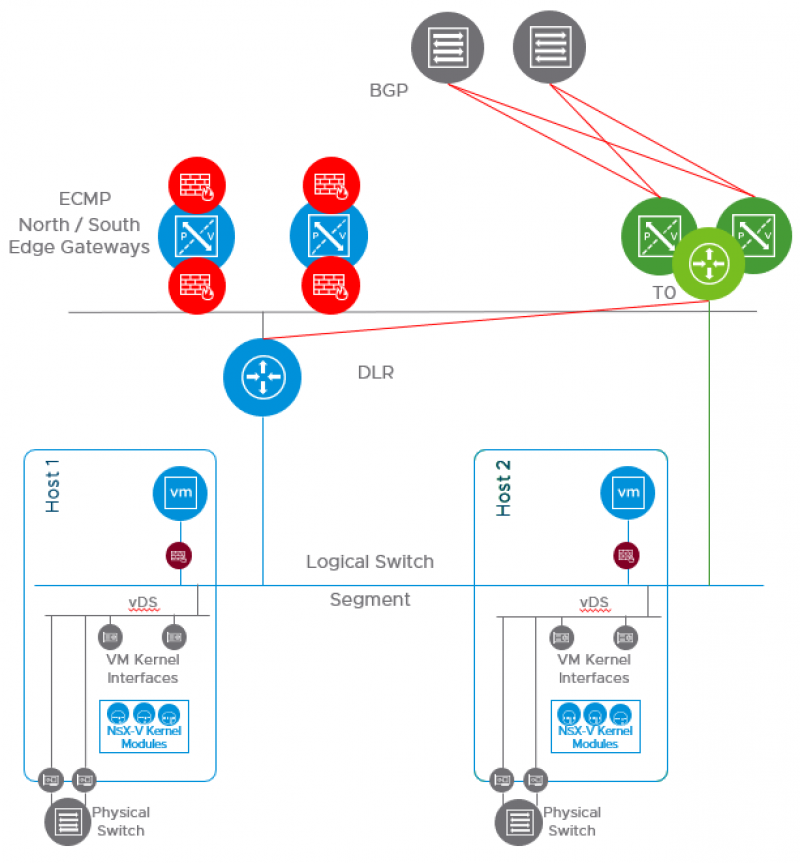
As said, during this step CDO is enabled and the Controllers are shut down.
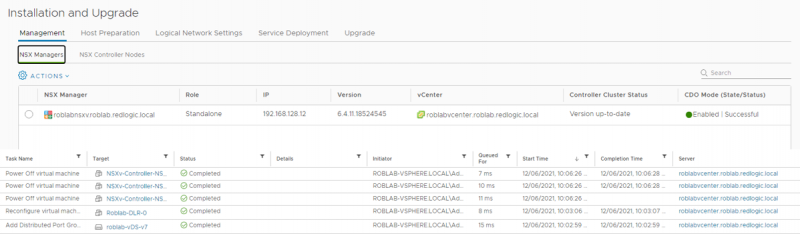
The NSX-V edge receives block rules to block all traffic to and from the NSX-V ESGs.
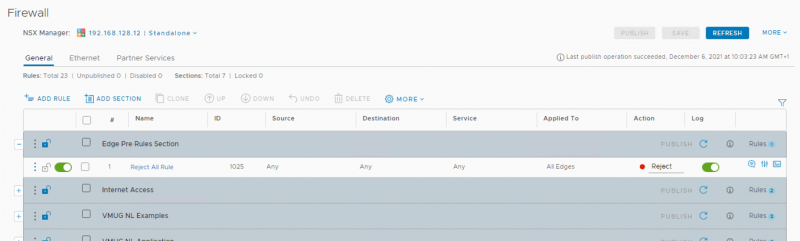
A static route in configured on the DLR to rout traffic from the DLR towards the NSX-T Tier-0 gateway.
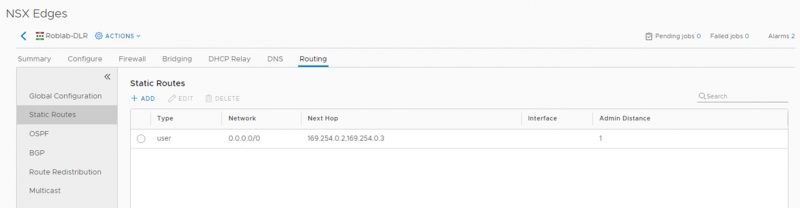
And the BGP peering’s are Established on the NSX-T Tier-0 gateway. Allowing the upstream routers to advertise routes to the lab environment.
At this point it is still possible to rollback the migration. Once you start the Migrate Host this is no longer possible from the migration coordinator.
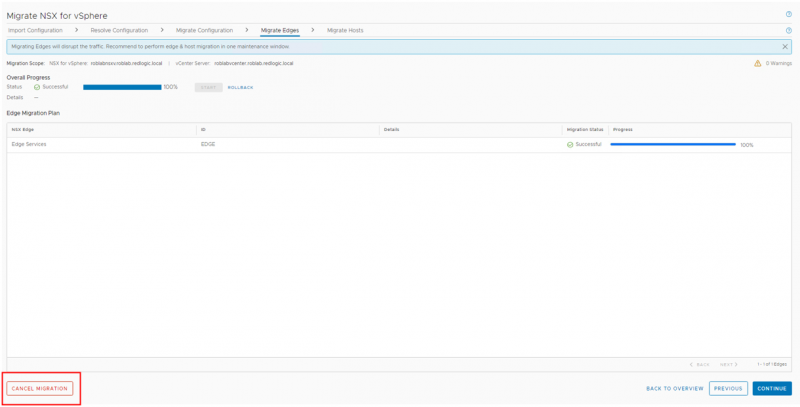
This concludes the final post in this series. Additional information on the Migrate Hosts step can be found in this blog and in the documentation of the migration coordinator.
Thanks for reading and hopefully this was helpful.
Please reach out if you still have any questions and I’ll try to answer them.
Questions, Remarks & Comments
If you have any questions and need more clarification, we are more than happy to dig deeper. Any comments are also appreciated. You can either post it online or send it directly to the author, it’s your choice.





 LinkedIn
LinkedIn
 Twitter
Twitter